
Government agencies face unprecedented cybersecurity challenges in 2025, with threats growing in sophistication and frequency. The NIST Cybersecurity Framework provides a comprehensive, standardized approach to protect critical infrastructure and sensitive data. This guide explores how government organizations can implement the framework to strengthen defenses, achieve compliance, and restore public trust. Learn about the 10 key ways NIST framework supports agencies, from structured risk management to cost-effective implementation, plus discover how secure chat platforms like Rocket.Chat integrate seamlessly with government security requirements.
Key takeaways:
- Ransomware attacks on government agencies surged with sophisticated nation-state actors targeting critical systems
- The NIST framework offers standardized protocols across agencies to manage evolving cyber threats effectively
- Implementation reduces supply chain vulnerabilities while supporting compliance with FedRAMP, FISMA, and zero-trust architectures
- Secure communication platforms are essential components of comprehensive NIST framework deployment
Government cybersecurity isn't just about protecting data—it's about national security and public trust. According to data from the Office of the Director of National Intelligence, ransomware attacks on U.S. government agencies jumped by 50% in 2023.
The start of 2025 wasn't much better, with the Cybersecurity and Infrastructure Security Agency (CISA) highlighting newly exploited vulnerabilities—such as CVE-2024-29059, an information disclosure flaw in Microsoft .NET Framework that could expose sensitive information.
The scale of government operations, coupled with sensitive data and critical infrastructure, makes security a daunting task. During the 2024 elections, the Department of Homeland Security (DHS) flagged election systems as prime targets for cyber threats. The risk isn't just operational—it's deeply political.
To address these challenges, regulatory frameworks are evolving rapidly. For example, 200 cloud services secured FedRAMP authorization in 2023 alone. At the core of these compliance efforts is the National Institute of Standards and Technology (NIST) Cybersecurity Framework—a set of robust guidelines for federal security strategies.
Let's explore how this framework is transforming government security and helping agencies protect critical assets in an increasingly hostile digital landscape.
Why governments need the NIST framework
Let's examine the reasons why governments must implement the NIST framework:
1. Escalating threats
Cyber threats to government agencies are more sophisticated and persistent than ever. Nation-state actors—particularly from China and Russia—are consistently probing U.S. systems. According to the Center for Strategic and International Studies, Chinese cyber espionage operations surged by 150% in 2024, with attacks against financial, media, manufacturing, and industrial sectors rising up to 300%.
Critical infrastructure isn't safe either. In February 2025, CISA issued seven new industrial control system (ICS) advisories. Election infrastructure remains a significant vulnerability, with DHS reporting increased foreign cyber influence. This underlines the need for a standardized and resilient security framework.
2. Resource allocation
Even with a $12.7 billion cybersecurity budget for FY 2024, federal agencies struggle with resource constraints. The cybersecurity workforce gap is stark—with CISA reporting over 400,000 unfilled cybersecurity positions nationwide.
The NIST framework can help agencies prioritize risks and allocate limited resources more effectively. By focusing on the most critical vulnerabilities first, agencies can maximize the impact of their security investments.
3. Regulatory requirements
Compliance isn't just a checkbox exercise. FISMA's 2024 updates mandate zero-trust architectures and enhanced risk assessments. FedRAMP adoption is also rising, with many cloud services currently in the certification process.
The NIST framework offers clear guidance to meet these evolving mandates while maintaining operational efficiency and organizational security standards.
4. Public trust
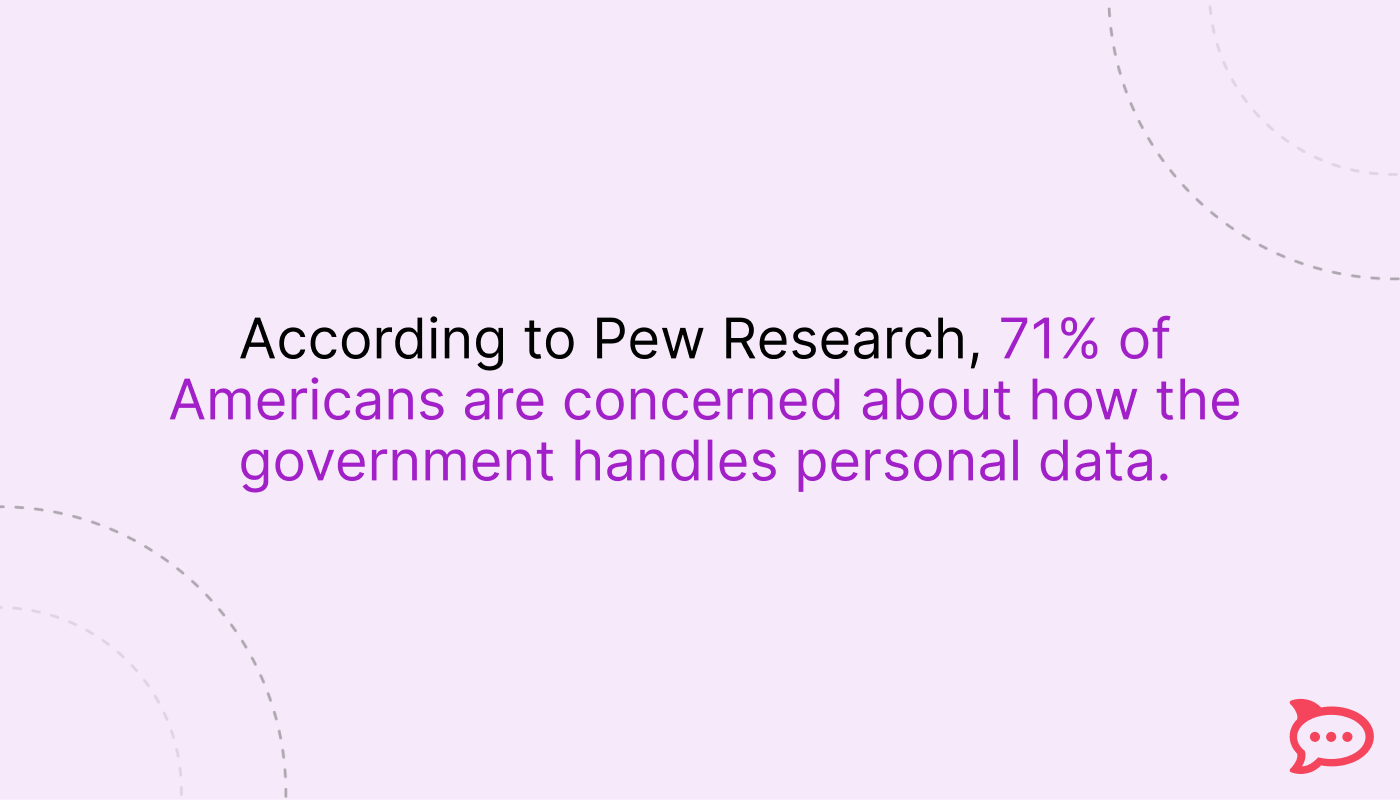
Public trust is fragile—especially when it comes to data security. According to Pew Research Center, 71% of Americans are concerned about how the government handles personal data.
Consistent, transparent security practices built on the NIST framework can help rebuild this trust and demonstrate accountability to citizens.
10 ways NIST framework supports government organizations
Now, let's explore how the NIST framework can sustain the cybersecurity posture of frontline government organizations:
1. Structured approach for complex organizations
Government agencies often struggle with disconnected security strategies. The NIST framework offers a standardized methodology that helps align cybersecurity practices across departments and agencies, improving coordination and response capabilities.
Here's how decision-makers can make it work:
- Standardize policies: Use the NIST framework to create uniform cybersecurity protocols across all agencies
- Enhance collaboration: Implement frameworks for multi-agency communication and incident response
- Adopt best practices: Leverage case studies like the Texas state government's successful NIST implementation
2. Risk management for government assets
Government data and critical infrastructure are prime targets for cyber threats. The NIST framework's risk management approach helps effectively identify, assess, and mitigate these risks through continuous monitoring and evaluation.
Leaders should focus on:
- Conduct risk assessments: Regularly evaluate supply chain risks and vulnerabilities
- Implement monitoring systems: Maintain real-time visibility into potential threats
- Strengthen vendor management: Apply stringent cybersecurity requirements to third-party vendors
3. Incident response readiness
When a cyber incident hits, reaction speed and effectiveness can make all the difference. The NIST framework's "Respond" function offers clear guidance for managing incidents—focusing on containment, eradication, and recovery.
To improve incident response, consider these steps:
- Develop response plans: Create playbooks for different types of incidents to ensure quick, standardized reactions
- Test strategies regularly: Conduct simulations and tabletop exercises to evaluate readiness
- Document and analyze incidents: Maintain detailed logs to improve response strategies and meet compliance requirements
4. Enhanced threat intelligence integration

The NIST framework encourages using threat data to anticipate and prevent attacks with agile emergency response capabilities. This proactive approach is critical for staying ahead of sophisticated threats.
To harness the power of threat intelligence:
- Leverage available resources: Utilize threat intelligence from CISA, DHS, and other government sources
- Automate threat detection: Integrate AI-driven tools like Splunk, IBM QRadar, and Palo Alto Networks Prisma within the NIST framework
- Foster intelligence sharing: Collaborate with other agencies through secure team chat platforms to strengthen defenses
5. Compliance and standards alignment
One of NIST's biggest advantages is its alignment with key federal standards like FedRAMP, FISMA, and NIST SP 800-53. This not only simplifies compliance but also accelerates cloud adoption for government agencies.
To align with compliance goals, consider this approach:
- Streamline compliance processes: Map existing practices to NIST standards
- Optimize cloud security: Ensure cloud services meet FedRAMP and NIST SP 800-53 guidelines
- Schedule regular audits: Maintain compliance and avoid regulatory pitfalls
6. Bulletproofing supply chain security
Supply chains are often the weakest link in cybersecurity. The NIST framework includes guidance on managing third-party risks. According to the U.S. Government Accountability Office, 37% of government system breaches in 2023 were linked to supply chain vulnerabilities.
Here's how to secure the supply chain:
- Vet third-party vendors: Conduct thorough security assessments before partnerships
- Monitor external risks: Establish continuous monitoring for third-party systems
- Enforce compliance: Require vendors to adhere to NIST cybersecurity standards
7. Stronger identity and access management (IAM)
Unauthorized access remains a top cybersecurity threat. The NIST framework emphasizes robust IAM practices, including multi-factor authentication and role-based access control, to reduce these risks.
To enhance IAM practices:
- Implement multi-factor authentication: Add extra layers of security to access points
- Apply role-based access controls: Limit data access based on job roles and responsibilities
- Regularly review access permissions: Ensure only authorized personnel have access to sensitive systems
8. Data protection and encryption
Data breaches are not just costly—they erode public trust. The NIST framework promotes encryption and strong data protection practices, ensuring that sensitive information remains secure both at rest and in transit.
What actions can enhance data security?
- Encrypt sensitive data: Use strong encryption standards for data at rest and in transit
- Use secure communication tools: Deploy encrypted messaging apps for all high-stake communications
- Implement data loss prevention (DLP) tools: Prevent unauthorized data transfers
- Apply data classification policies: Identify and secure sensitive data based on its classification level
9. Continuous improvement in the public sector
The cybersecurity landscape evolves quickly. The NIST framework encourages regular assessments and adaptations to keep pace with evolving threats. With 50% of federal agencies now adopting zero-trust models, continuous improvement is critical.
Keeping up with evolving threats requires:
- Invest in training: Leverage programs like CISA's Cyber Defense Skilling Academy
- Update security protocols: Adapt regularly to address new threats
- Foster innovation: Pilot new security technologies and frameworks
10. Cost-effective implementation
Budgets are tight, but the NIST framework helps optimize spending through strategic resource allocation. Shared services can reduce cybersecurity costs, offering a practical approach for budget-conscious agencies.
When budgets are tight, here's how to maximize impact:
- Utilize shared services: Reduce costs through shared cybersecurity resources and tools
- Evaluate ROI: Ensure cybersecurity investments deliver measurable value
- Apply for funding: Seek grants and federal programs that support cybersecurity initiatives
- Find open-source alternatives: Open-source platforms can significantly cut costs while offering robust features
Rocket.Chat: the perfect solution for NIST framework implementation
When it comes to secure collaboration tools, Rocket.Chat offers tailored features for government needs that align perfectly with NIST framework requirements:
- On-premise deployment: Complete data control and compliance with strict data residency requirements
- FedRAMP-ready and zero trust compatible: Integrates seamlessly with government compliance frameworks, including GDPR, CCPA, HIPAA, and FedRAMP
- Advanced security features: End-to-end encryption, multi-factor authentication, and role-based access control
- Federated messaging: Enables secure communication across agencies while maintaining data integrity
- Audit and compliance tools: Built-in logging and auditing features to meet regulatory needs
- Integration capabilities: Connects with existing government systems, reducing deployment complexity
- Incident management features: Supports mission-critical communications with dedicated channels and automation
Rocket.Chat for governments across the globe
Rocket.Chat isn't just any messaging platform—it's a trusted solution for governments needing secure, compliant communication:
- In the U.S., federal entities like the Department of Defense use it for defense communication systems, keeping operations compliant and flexible
- Brazil's Public Defender's Office of São Paulo uses Rocket.Chat to keep legal teams connected while ensuring tight data control
- Multiple government communication implementations across federal, state, and local levels demonstrate proven reliability
Explore how federal governments, EU agencies, and state/local governments have implemented Rocket.Chat for government chat solutions that meet the strictest security standards.
Supporting military and defense operations
For military applications requiring military communication capabilities, Rocket.Chat provides:
- Air-gapped deployment: Complete isolation for air-gapped collaboration in classified environments
- Military-grade encryption: Support for military messaging with advanced encryption protocols
- Out-of-band communication: Dedicated channels for out-of-band communication during critical operations
- Tactical deployment: Lightweight deployment options for military chat in field operations
These capabilities make Rocket.Chat an ideal choice for defense organizations requiring both security and operational flexibility.
Enhancing workplace collaboration
Beyond government and military applications, Rocket.Chat supports comprehensive workplace team communication needs:
- Unified platform: Single chat app for all organizational communication needs
- Scalability: From small teams to large government agencies with thousands of users
- Integration ecosystem: Connect with existing tools and workflows
- Mobile support: Government messaging app available across all devices
As one of the leading instant messaging platforms, Rocket.Chat delivers enterprise-grade features with government-level security. Organizations can leverage encrypted messaging capabilities while maintaining full control over their data and infrastructure.
Final thoughts
The NIST Cybersecurity Framework, combined with advanced secure collaboration tools like Rocket.Chat, empowers government agencies to build robust defenses, maintain compliance, and restore public trust.
According to IBM's Cost of a Data Breach Report, organizations with comprehensive security frameworks experience 108 days faster breach detection and containment, saving an average of $1.76 million per incident. The framework's structured approach helps agencies address the growing complexity of cyber threats while managing limited resources effectively.
Implementing these strategies isn't just about checking regulatory boxes—it's a strategic move toward a safer, more cyber-resilient government infrastructure that protects citizens and maintains operational continuity.
To try out Rocket.Chat, schedule a demo now!
Frequently asked questions about the NIST cybersecurity framework
What is the NIST cybersecurity framework and why do government agencies need it?
The NIST Cybersecurity Framework is a voluntary set of standards and best practices developed by the National Institute of Standards and Technology to help organizations manage cybersecurity risks. Government agencies need it because cyber threats are escalating—with ransomware attacks on federal systems increasing 50% in 2023 and nation-state actors continuously probing critical infrastructure. The framework provides a common language for cybersecurity across agencies, helps prioritize limited resources effectively, supports compliance with regulations like FISMA and FedRAMP, and rebuilds public trust through transparent security practices.
What are the six core functions of NIST cybersecurity framework 2.0?
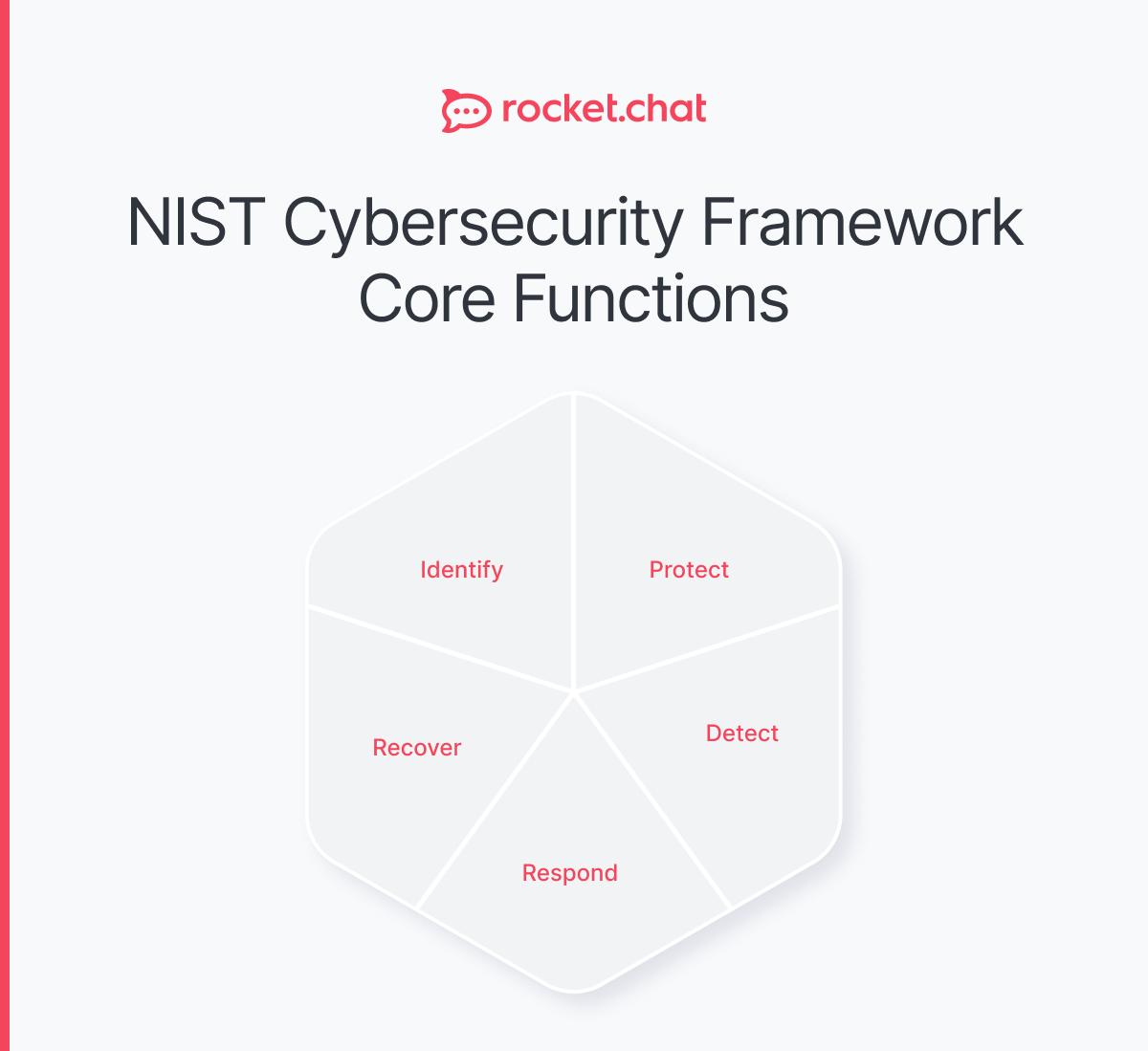
The NIST framework 2.0 organizes cybersecurity into six interconnected functions: Govern establishes cybersecurity strategy and oversight at the executive level. Identify catalogs assets, systems, and risks across the organization. Protect implements safeguards like encryption and access controls. Detect monitors for security events and anomalies in real-time. Respond contains and mitigates incidents when they occur. Recover restores operations and applies lessons learned. These functions work together as a continuous cycle, with the new "Govern" function added in version 2.0 to emphasize leadership accountability.
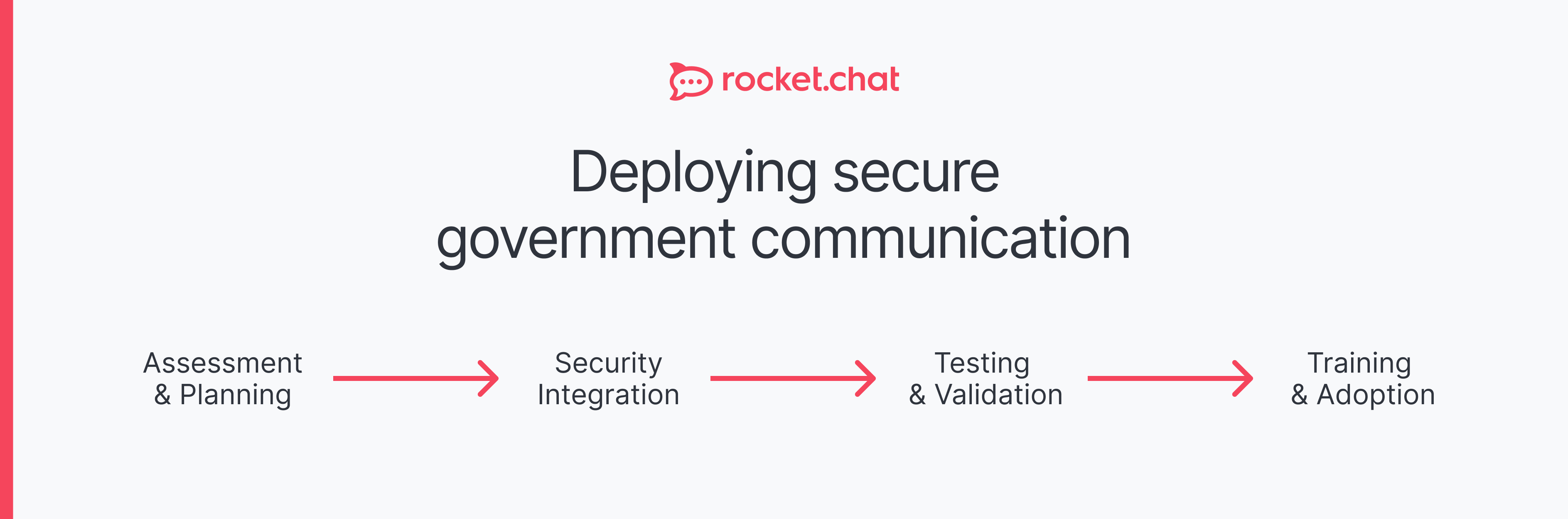
How do government agencies implement the NIST cybersecurity framework?
Implementation follows a structured seven-step process: First, define objectives and scope based on agency priorities. Second, assess current security posture and identify gaps. Third, conduct comprehensive risk assessments of systems and data. Fourth, create a target profile defining desired security outcomes. Fifth, prioritize gaps between current and target states. Sixth, develop an action plan with timelines and resource allocation. Finally, implement controls and establish continuous monitoring. Throughout this process, agencies should deploy secure communication platforms that support NIST requirements—including end-to-end encryption, audit logging, and compliance-ready features.
Is NIST framework compliance mandatory for government organizations?
The NIST framework itself is voluntary guidance, but related requirements vary by agency type. Federal agencies must comply with FISMA requirements and related NIST standards like SP 800-53. Government contractors handling sensitive data must meet NIST SP 800-171 controls. State and local agencies aren't federally mandated but often adopt the framework to qualify for federal funding or demonstrate security maturity. While the CSF provides flexible guidance, agencies face practical mandates through procurement requirements, grant conditions, and increasing pressure to demonstrate cybersecurity due diligence following high-profile breaches.
What tools and platforms support NIST framework implementation for government?
Successful NIST implementation requires integrated security and collaboration tools across all six functions. For governance, agencies need policy management and risk assessment platforms. The Protect function requires identity management, encryption tools, and secure communication systems like Rocket.Chat that offer on-premise deployment, end-to-end encryption, and FedRAMP-ready compliance. Detection needs SIEM systems and threat intelligence platforms. Response requires incident management tools and secure coordination channels. Organizations should prioritize tools that provide audit trails, support zero-trust architectures, enable federated communication across agencies, and integrate with existing government IT infrastructure.
Frequently asked questions about <anything>


- Digital sovereignty
- Federation capabilities
- Scalable and white-labeled


- Highly scalable and secure
- Full patient conversation history
- HIPAA-ready

for mission-critical operations
- On-premise and air-gapped ready
- Full control over sensitive data
- Secure cross-agency collaboration
%201.svg)

- Open source code
- Highly secure and scalable
- Unmatched flexibility


- End-to-end encryption
- Cloud or on-prem deployment
- Supports compliance with HIPAA, GDPR, FINRA, and more


- Supports compliance with HIPAA, GDPR, FINRA, and more
- Highly secure and flexible
- On-prem or cloud deployment



.avif)


